CVE-2020-10557
This post a brief description of the discovery and development of CVE-2020-10557.
Background
AContent is a free web content and authoring tool made by the same authors as Atutor. This application has a history of vulnerabilities on Exploit-db, thus I expected to find more in the newest release. For the purposes of CVE testing, I aim to avoid accounts with administrator privileges to better gauge just how much damage a malicious low privileged user could accomplish. Conveniently, AContent allows for open registration of both student and teacher accounts. Since the teacher accounts have slightly more privileges, I decided to use that account.
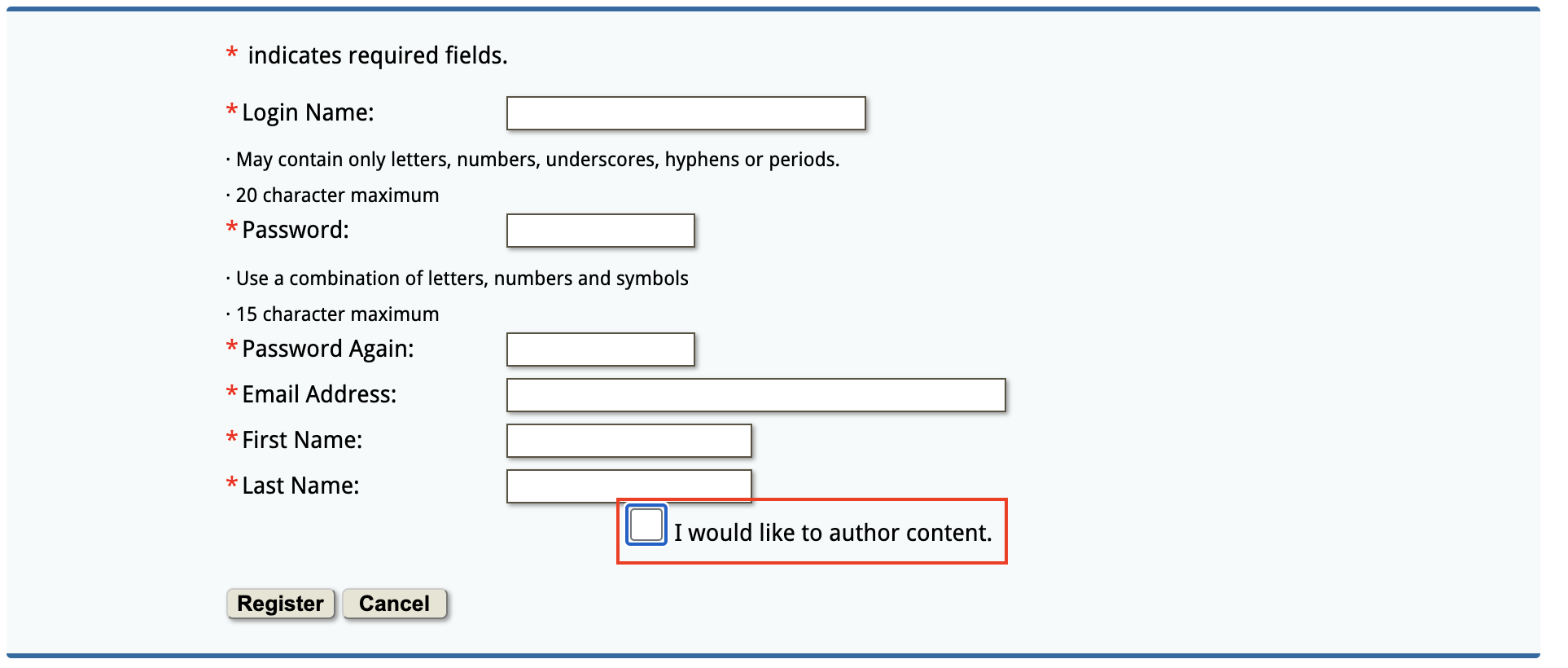
Figure 1: Registration Page with Check Box for Content Creator Account
After further exploration of the site I discovered an area for file uploads, always a great place to begin looking for unusual behavior or potential vulnerabilities. Shortly after trying some combinations of file extension bypass payloads, I determined that both .php7 and .phtml were not rejected by the web application. Thus, one could upload a malicious web shell in order to execute commands against the web server.
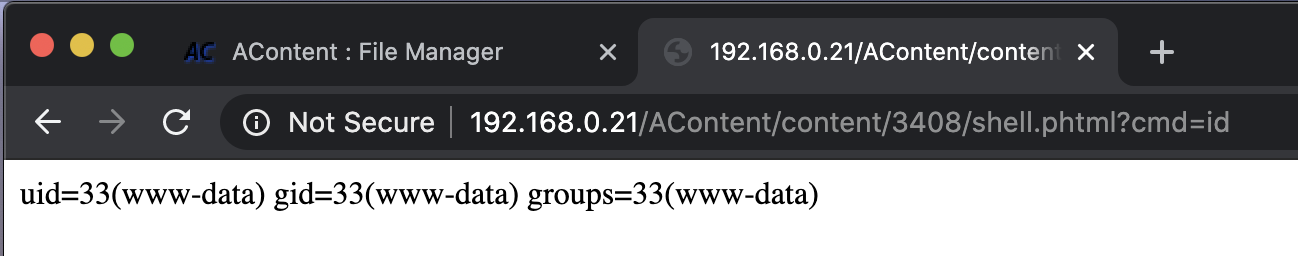
Figure 2: Successful File Upload Restriction Bypass and RCE
The Exploit
Great, so now we at least know we have a CVE for unrestricted file upload leading to RCE; however, with this CVE I wanted to try something a little different. I wanted to attempt to script a fully functional exploit to allow a user to execute commands against the server via their terminal without needed to manually exploit.
After struggling for way too long with Python3 and troubleshooting silly typos, I eventually got a semi-functional exploit working. I say “semi-functional” as there are two caveats. First, the user must supply a valid session cookie via command line parameters, meaning they must log in and determine this using document.cookie. Originally my aim was to simply pass username and password into the exploit via command line; however, I encountered some errors that I was unable to troubleshoot and thus determined using the cookie would be simpler. Second, the user must also know their author number. This number can easily be determined with Burp Suite. Alternatively, it can be brute forced as the number simply increments by 1 with each new account created, thus one could script the exploit until they see a successful completion. The completed exploit can be found here.
Now, without further delay, I present CVE-2020-10557!
python3 cve-2020-10557.py -url http://192.168.0.21/AContent/ -cookie 58n37v64bq3teoi097koae8f01 -author 9
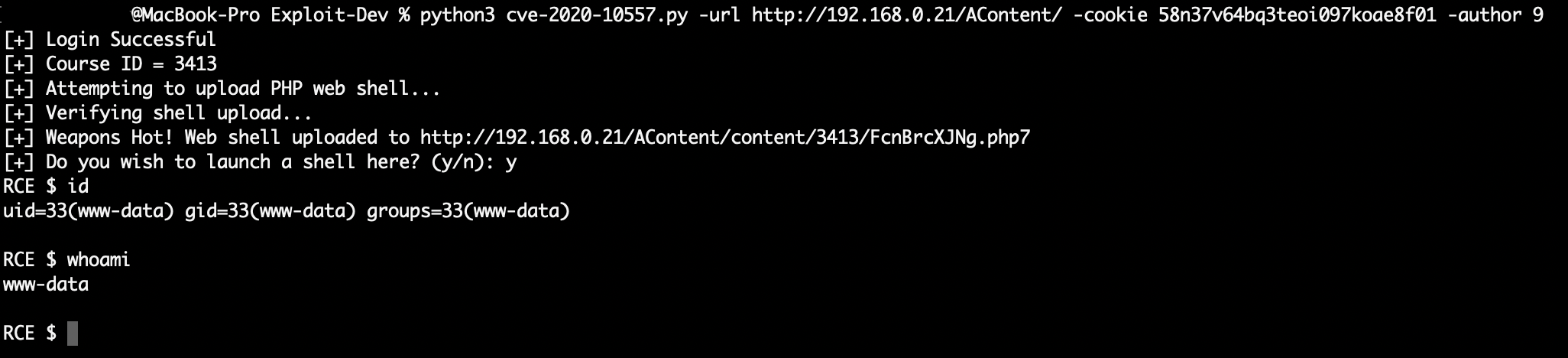
Figure 3: Successful Exploitation via Command Line
Impact
After reaching out to the developer, I saw that this project has been unmaintained for two years. I highly recommend that the two live websites still running AContent find another web application to meet their needs.
Figure 4: Sites running AContent
Acknowledgements
I would like to thank m0rph-1 and Tib3rius for putting up with all my amateur Python coding questions.



